Introduction to Container Security
Container security encompasses practices, tools, and measures to protect the entire lifecycle of containerized applications. Containers offer portability and consistency across environments, crucial for modern software development. However, their unique structure presents distinct security challenges that need to be addressed.
Why Container Security is Crucial
Security breaches can occur at any stage of the software development lifecycle (SDLC), making integrated security measures essential. Vulnerabilities can be introduced during development, deployment, and runtime stages, necessitating comprehensive protection throughout the lifecycle.
Key Components of Container Architecture to Secure
- Container Images: Scan for vulnerabilities and use trusted, minimal images.
- Registries: Control access to image repositories to prevent unauthorized changes.
- Orchestrators: Properly configure security controls for managing container deployment.
- Container Engine: Ensure the runtime environment is secure to prevent unauthorized access.
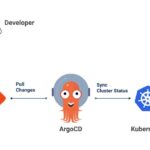
Shared Responsibility Model
In container security, both cloud service providers and users share responsibilities. Providers secure the underlying infrastructure, while users are responsible for securing their workloads within the cloud.
Common Challenges in Securing Containers
- Complexity: Containers add a new layer of complexity to IT environments.
- Vulnerability Management: Managing vulnerabilities in container images with multiple layers.
- Configuration Errors: Misconfigurations can lead to security incidents.
- Visibility and Monitoring: The ephemeral nature of containers makes monitoring challenging.
- Supply Chain Attacks: Containers often rely on components from various sources, posing a risk if any link is compromised.
Ground-Level Practices to Fortify Container Security
- Ensuring Secure Container Images: Verify image origins and perform regular scans.
- Reducing the Attack Surface: Eliminate unnecessary software and services.
- Utilizing Robust Container Security Tools: Use tools for vulnerability scanning, configuration checking, and runtime monitoring.
- Preparing an Incident Response Plan: Have a plan for identifying and recovering from security incidents.
- Implementing Regular Audits: Regularly audit container activities, configurations, and components.
- Enforcing Strict Access Controls: Use Role-Based Access Control (RBAC) and the principle of least privilege.
- Updating and Patching Regularly: Apply updates and patches to the container runtime, orchestration tools, applications, and host systems.
- Protecting Container Orchestration: Secure API access, use network policies, and regularly check configurations.
Open-Source Container Security Tools by Use Case
- Ensuring Secure Container Images: Clair, Docker Bench
- Reducing the Attack Surface: CIS Docker Benchmark, Kubernetes Pod Security Policies
- Utilizing Robust Container Security Tools: Falco, OpenSCAP
- Preparing an Incident Response Plan: TheHive, FIR (Fast Incident Response)
- Implementing Regular Audits: Auditd, GRR
- Enforcing the Principle of Least Privilege: Kubernetes RBAC, Docker user namespaces
- Updating and Patching Regularly: Watchtower, Anchore Engine
- Protecting Container Orchestration: Kubernetes Network Policies, RBAC
Going Beyond the Basics with Wiz
Wiz provides advanced container security solutions, offering tools to secure container images across their lifecycle. Key features include:
- Scanning for vulnerabilities, malware, and exposed secrets.
- Evaluating configurations and Kubernetes architecture for security issues.
- Preventing excessive permissions for containers.
- Contextual cloud risk assessments.
- Integration with CI/CD pipelines for early security enforcement.
- Admission Controller to protect Kubernetes clusters from unsafe deployments.
By leveraging Wiz, organizations can proactively protect their containerized environments and ensure consistent application of security best practices.
Conclusion
Securing container environments is an ongoing journey. By implementing the outlined best practices and leveraging advanced tools like Wiz, organizations can navigate the complexities of container security effectively. Take the next step in your container security journey with Wiz and start your demo today!
Register for Demo
Reference to the Article : Wiz
Follow us for Updates