Kubernetes has become the go-to platform for deploying containerized applications. As its usage grows, the need for robust backup solutions becomes even more critical. This guide introduces K8up, a Kubernetes Operator designed to streamline backups for Persistent Volumes (PVCs) and applications. We’ll delve into K8up’s architecture, installation, and explore its functionalities through code examples.
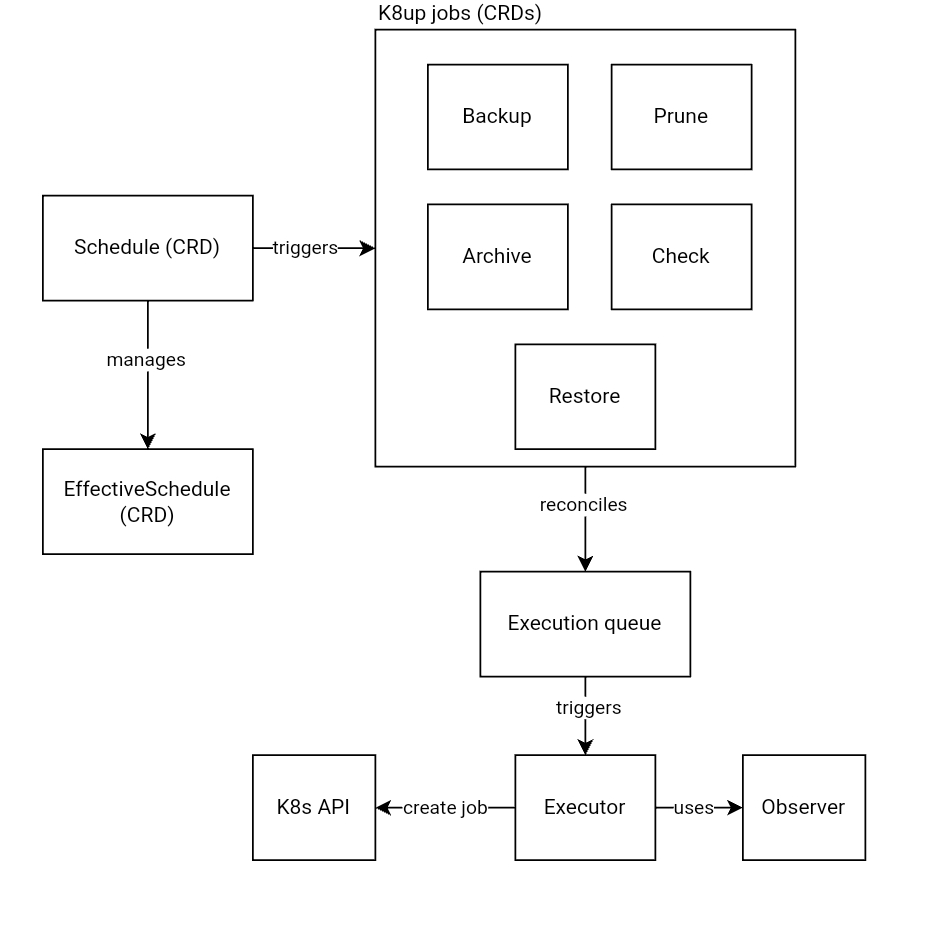
K8up’s Architecture
K8up’s core consists of two key components:
- K8up Operator: Deployed as a cluster-wide operator, it manages Backup and Schedule resources. Based on these schedules, the Operator creates backup jobs. It scans namespaces for matching PVCs and leverages Restic to back up data to the configured storage.
- Restic Wrapper (k8up Restic): This component executes backup commands within Pods. When a backup is triggered, the Operator creates a corresponding Job. The Restic wrapper, running in a container, performs the actual backup using the Restic binary.
Installation
Let’s install K8up on your Kubernetes cluster using Helm:
- Add the K8up Helm repository:
helm repo add k8up-io https://k8up-io.github.io/k8up
- Install K8up:
helm install k8up k8up-io/k8up
- Apply CRDs (Custom Resource Definitions):
kubectl apply -f https://github.com/k8up-io/k8up/releases/download/k8up-4.4.3/k8up-crd.yaml
General Backups
To create a general backup with K8up, define a Backup resource in a YAML file. Here’s an example:
YAML
# backup.yaml
apiVersion: k8up.io/v1
kind: Backup
metadata:
name: k8up-general-backup
spec:
backend:
repoPasswordSecretRef:
name: backup-repo
key: password
s3:
endpoint: http://minio:9000
bucket: backups
accessKeyIDSecretRef:
name: minio-credentials
key: username
secretAccessKeySecretRef:
name: minio-credentials
key: password
This configuration instructs K8up to back up data to a specified S3-compatible storage.
Application-Aware Backups
K8up’s application-aware backups let you execute commands within Pods. Here’s an example for a PostgreSQL database:
YAML
# postgres-backup.yaml
apiVersion: k8up.io/v1
kind: Backup
metadata:
name: k8up-postgres-backup
spec:
backend:
repoPasswordSecretRef:
name: backup-repo
key: password
s3:
endpoint: http://minio:9000
bucket: postgres-backups
accessKeyIDSecretRef:
name: minio-credentials
key: username
secretAccessKeySecretRef:
name: minio-credentials
key: password
template:
metadata:
labels:
app: postgres
annotations:
k8up.io/backupcommand: sh -c 'pg_dump -U $POSTGRES_USER -h $POSTGRES_HOST $POSTGRES_DB > /data/backup.sql'
This Backup resource not only specifies the backend but also provides a tailored command (pg_dump) for PostgreSQL.
Pre-Backup Pods
K8up can execute backup commands in existing Pods. However, in some cases, you might want to start a specific Pod for the backup. This is where Pre-Backup Pods come in handy. Here’s how to define one:
YAML
# pre-backup-pod.yaml
apiVersion: k8up.io/v1
kind: PreBackupPod
metadata:
name: k8up-mysqldump
spec:
backupCommand: sh -c 'mysqldump -u $MYSQL_USER -p$MYSQL_PASSWORD -h $MYSQL_HOST --all-databases > /data/backup.sql'
pod:
spec:
containers:
- env:
- name: MYSQL_USER
value: root
- name: MYSQL_PASSWORD
value: topsecret
- name: MYSQL_HOST
value: mysql.example.Reference to the Article- Kubetools
Follow us for more Updates