Smarter DevOps: AI’s Role in CI/CD Automation
As software development evolves, speed, reliability, and automation have become essential. Organizations are shifting from traditional DevOps to an AI-driven approach to enhance Continuous Integration and Continuous Deployment (CI/CD) pipelines. AI’s ability to analyze vast datasets, automate repetitive tasks, and predict failures is reshaping the way DevOps teams operate. 🚀 How is AI transforming DevOps?…

Beyond Manual Operations: Why IT Automation is a Game-Changer
Modern IT infrastructure is complex, dynamic, and demands speed, scalability, and efficiency. Manual management of servers, networks, databases, and security protocols is no longer feasible in an era of cloud computing, DevOps, and AI-driven operations. This is where IT automation steps in—orchestrating workflows, provisioning resources, managing configurations, and ensuring security compliance without human intervention. But…

From GDPR to CCPA: Adapting to Evolving Data Regulations
In today’s digital landscape, data has become one of the most valuable assets for businesses and individuals alike. However, with the increasing amount of personal and sensitive information being shared and stored online, the risks of data breaches, cyber threats, and misuse have also surged. This has made data privacy and compliance more critical than…

AI in Cybersecurity: Strengthening Defense, One Algorithm at a Time!
In today’s digital landscape, cyber threats are evolving at an unprecedented rate. Traditional security measures are no longer sufficient to combat sophisticated attacks. This is where Artificial Intelligence (AI) and Machine Learning (ML) come into play, transforming cybersecurity by enhancing threat detection, response, and prevention mechanisms. The integration of AI-driven technologies is revolutionizing the way…
From Bits to Qubits: The Quantum Future of IT Operations
Introduction The IT industry has long been driven by Moore’s Law—the observation that the number of transistors on a chip doubles approximately every two years. However, as we approach the physical limits of silicon-based computing, quantum computing is emerging as a game-changer. By leveraging quantum mechanics, quantum computers can solve problems that would take classical…

Revolutionizing IT with Blockchain: A New Era of Security and Trust
Introduction Blockchain is often synonymous with cryptocurrencies like Bitcoin, but its potential extends far beyond digital currency. In the IT sector, blockchain is revolutionizing data security, system transparency, and decentralized infrastructure. From secure data sharing to enhanced cybersecurity, blockchain is redefining how businesses manage IT operations. How Blockchain is Impacting IT 1. Enhanced Cybersecurity Cyber…
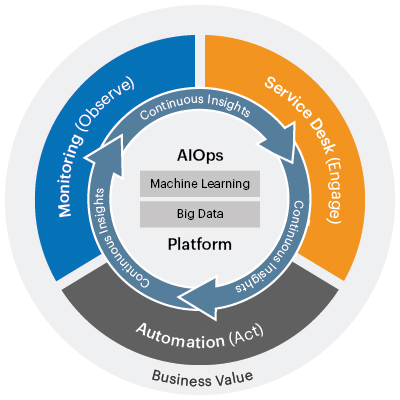
AI in IT Ops: Enhancing Performance & Security
In today’s fast-paced digital world, IT operations are more complex than ever. With increasing workloads, intricate infrastructures, and rising security threats, managing IT systems manually is no longer sustainable. This is where Artificial Intelligence for IT Operations (AIOps) comes into play. AIOps is revolutionizing IT management by leveraging AI and automation to streamline processes, enhance…

Master Generative AI with Google’s Free 5-Day Intensive
Generative AI (Gen AI) is revolutionizing the way we interact with technology, from text generation to intelligent automation. If you’re eager to deepen your understanding and get hands-on experience with the latest advancements in Gen AI, Google’s 5-Day Generative AI Intensive Course is the perfect opportunity. Back by popular demand after attracting over 140,000 developers…

Unlock SOC Excellence: Top Free Courses for Security Professionals
Level Up Your SOC Skills: Free Training to Master Security Operations In the fast-paced world of cybersecurity, a skilled Security Operations Center (SOC) team is your first line of defense. But staying ahead of evolving threats requires continuous learning and development. Fortunately, there are several excellent free training resources available to help you and your team hone…

Enable modern privileged access management with HashiCorp Boundary
September 18 12:00 PM EDT | September 19 9:00 AM BST | September 25 10:00 AM SGT Speakers : Dan Rohan Product Manager, Boundary Van Phan Technical Product Marketing Manager, Boundary and Consul Revolutionizing Secure Access with HashiCorp Boundary: Adopting a Modern, Identity-Driven Approach Traditional workflows for accessing infrastructure resources and applications often rely heavily…
